Protecting sensitive information against security threats is paramount for businesses of all sizes. ISO 27001 stands at the forefront of information security management, offering a systematic and structured framework that helps organizations secure their information assets. This international standard provides the specifications for an Information Security Management System (ISMS), which is instrumental in identifying, managing, and reducing the range of threats to which information is regularly subjected.
This article overviews everything core to ISO 27001 — namely, its controls, specifically those outlined in Annex A. These controls are not only fundamental to the certification process but are also essential for establishing, implementing, maintaining, and continually improving an ISMS. ISO 27001 includes 114 controls in 14 domains, each addressing specific aspects of information security, from risk assessment to HR security, all the way to encryption and operational procedures.
Understanding these controls and the structure of Annex A is crucial for any organization aiming to achieve ISO 27001 certification. This guide will provide an in-depth look at what these controls entail, how they are implemented, and their role in the broader context of information security management. Additionally, we will explore the recent updates to the standard, including new controls that reflect the evolving landscape of cyber threats. By the end of this article, organizations should have a clearer understanding of how to navigate the complexities of ISO 27001 and enhance their information security efforts effectively.
Overview of ISO 27001 Annex A Controls
Annex A of ISO 27001 serves as a critical component within the standard, acting as a comprehensive catalog of information security controls that organizations can implement to mitigate risks and enhance their security posture. This annex is designed to support the requirements specified in the main body of the standard by providing a detailed framework of controls that are tailored to address specific security needs.
What are Annex A Controls?
Annex A of ISO 27001 contains a structured set of 114 controls divided into 14 distinct domains. These controls are optional and are to be implemented based on the organization's industry, risk environment, and specific security requirements. The controls range from policies for information security, organization of information security, human resource security, asset management, access control, cryptography, physical and environmental security, to operations security, communications security, system acquisition, development and maintenance, supplier relationships, information security incident management, information security aspects of business continuity management, and compliance.
Framework and Total Number of Controls
The framework provided by Annex A is meticulously designed to be comprehensive yet flexible, allowing organizations to adopt an adaptive approach to security. With 114 controls, organizations can select which specific controls are relevant to their operational needs based on a thorough risk assessment. The flexibility of this approach is one of the reasons ISO 27001 is highly regarded among information security standards.
Division into 14 Domains
The division of controls into 14 domains facilitates a systematic approach to implementing security measures, ensuring that all aspects of information security are covered. Each domain targets a different aspect of information security management, making it easier for organizations to focus on specific areas of concern. For instance, the 'Human Resource Security' domain deals with ensuring that employees, contractors, and third-party users understand their responsibilities and are suitable for the roles they are considered for, while 'Access Control' focuses on limiting access to information and information processing facilities.
This structured division not only simplifies the implementation process but also aids in thorough documentation and consistent application of practices across various departments and functions within the organization.
In the following section, we will delve deeper into each of the 14 domains, providing insights into their specific controls and the integral role they play in fortifying an organization’s information security strategies.
Deep Dive into the 14 Domains of ISO 27001
ISO 27001 organizes its Annex A controls into 14 domains, each addressing different security aspects necessary for comprehensive information security management. Understanding these domains is crucial for implementing effective security measures tailored to an organization's specific risks and needs. Here’s a closer look at each domain and the types of controls it encompasses:
1. Information Security Policies (A.5)
This domain ensures that policies for information security are established, published, implemented, and reviewed based on organizational needs and security standards. Controls focus on developing a framework to manage and review the effectiveness of information security policies regularly.
2. Organization of Information Security (A.6)
Controls in this domain deal with the management of information security within the organization and with external parties. It includes aspects like internal organization, mobile device and teleworking management, ensuring that security practices align with business operations.
3. Human Resource Security (A.7)
Before, during, and after employment, this domain outlines how to address the roles and responsibilities of employees, contractors, and third-party users in protecting organizational assets. Key controls include screening, terms and conditions of employment, and the management of changes in employment.
4. Asset Management (A.8)
Focusing on identifying organizational assets and defining appropriate protection responsibilities, this domain includes controls related to asset inventory, acceptable use, and information classification to ensure assets receive an appropriate level of protection.
5. Access Control (A.9)
This domain deals with ensuring that access to systems and data is controlled and restricted based on the business and security requirements. Controls cover user access management, user responsibilities, and system and application access control.
6. Cryptography (A.10)
Controls in this domain guide the use and management of cryptographic technologies to protect the confidentiality, authenticity, and integrity of information.
7. Physical and Environmental Security (A.11)
This domain involves securing physical access to information systems, preventing unauthorized physical access, damage, and interference to the organization’s premises and information.
8. Operations Security (A.12)
It includes controls designed to ensure secure operations through correct and secure operations of information processing facilities. It covers areas like operational procedures, protection from malware, backup, logging and monitoring, and control of operational software.
9. Communications Security (A.13)
This domain addresses the protection of information in networks and its support of information transfer within and between organizations. It includes network security management and information transfer policies and procedures.
10. System Acquisition, Development, and Maintenance (A.14)
Controls here ensure that information security is an integral part of information systems across the lifecycle, including requirements analysis and secure system engineering principles.
11. Supplier Relationships (A.15)
This domain manages risks associated with access to the organization's assets by external suppliers. Controls include supplier service delivery management, monitoring supplier services, and managing changes to supplier services.
12. Information Security Incident Management (A.16)
This domain outlines the management of information security incidents and improvements. Controls help ensure a consistent and effective approach to handling and communicating security incidents.
13. Information Security Aspects of Business Continuity Management (A.17)
Controls in this domain ensure the continuation of security measures and resilience in the event of adverse conditions. This includes information security continuity, redundancies, and testing of business continuity plans.
14. Compliance (A.18)
The final domain involves controls ensuring compliance with legal, statutory, regulatory, and contractual requirements, and with internal policies and standards through regular reviews.
Each domain plays a vital role in crafting a robust information security management system. By breaking down the requirements into these specific areas, ISO 27001 helps organizations systematically manage and mitigate their information security risks. The following sections will explore key differences between ISO 27001 and ISO 27002 and provide practical guidance on implementing these controls.
Key Differences and Relations: ISO 27001 Annex A vs. ISO 27002
Understanding the relationship between ISO 27001 and ISO 27002 is crucial for organizations looking to enhance their information security management systems. While both are designed to help organizations secure their information resources, they serve distinct purposes and are used in complementary ways.
ISO 27001 - The Certification Standard
ISO 27001 is an auditable standard that specifies the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). The essence of ISO 27001 is its comprehensive approach to security, which includes the assessment and treatment of information security risks tailored to the needs of the organization. This standard is what organizations get certified against when they demonstrate that their ISMS meets the criteria set out by the standard.
ISO 27002 - The Guideline for Controls
ISO 27002, on the other hand, acts as a best practice guideline that provides more detailed guidance on how to implement the specific controls listed under Annex A of ISO 27001. While ISO 27001 lists what controls should be considered, ISO 27002 explains how to implement these controls effectively. It is worth noting that ISO 27002 is advisory, providing recommendations rather than requirements; therefore, it is not used for certification purposes.
The Complementarity of Both Standards
The complementary nature of ISO 27001 and ISO 27002 is significant. ISO 27001 provides the certification framework and requires organizations to select controls based on their specific risk scenarios. ISO 27002 offers detailed guidance on those controls, making it an invaluable resource for organizations seeking practical advice on how to implement the controls effectively.
Key Differences
- 1. Purpose and Use: ISO 27001 is used for certification. It sets out the criteria that organizations must meet to establish a compliant ISMS. ISO 27002 is a guidance document that helps organizations implement the controls necessary for an effective ISMS but is not used for certification.
- 2. Structure: ISO 27001 is structured around a risk management process that requires identification, analysis, and treatment of risks, while ISO 27002 provides a detailed catalogue of security control guidelines that help mitigate these risks.
- 3. Flexibility: ISO 27001 requires organizations to perform a risk assessment and then choose appropriate controls from Annex A or other controls that might be more suited to their specific circumstances. ISO 27002, although detailed, serves as a guide and thus provides flexibility in how controls are implemented.
In practice, organizations looking to achieve ISO 27001 certification will benefit from using ISO 27002 to understand and implement the controls effectively. By integrating both standards, organizations can develop a robust information security management system tailored to their unique environments and challenges.
In the next section, we will delve into the practical steps involved in implementing ISO 27001 controls, providing guidance on assessing and prioritizing controls for effective ISMS development.
Implementing ISO 27001 Controls
Successfully implementing ISO 27001 controls is essential for organizations seeking to establish a robust Information Security Management System (ISMS). This process involves several key steps, starting from understanding the organization's specific security needs to ensuring continuous improvement. Here, we provide a structured approach to help organizations effectively implement ISO 27001 controls.
Step 1: Conduct a Risk Assessment
The first step in implementing ISO 27001 controls is to conduct a comprehensive risk assessment. This involves identifying potential security threats and vulnerabilities that could affect the organization's information assets. The goal is to determine the likelihood and potential impact of these risks, which will guide the selection of appropriate controls.
- Identify Assets: List all information assets that need protection, including data, systems, and services.
- Identify Threats and Vulnerabilities: Determine what could potentially harm the assets, such as cyber-attacks, human error, or natural disasters.
- Assess Risks: Evaluate the likelihood and impact of each identified risk on the organization.
Step 2: Select Appropriate Controls
Based on the risk assessment, select controls from ISO 27001 Annex A that address the identified risks. Not all 114 controls will be relevant to every organization; the selection should be tailored to the specific risks and business context.
- Customize Control Selection: Choose controls that specifically mitigate identified risks.
- Consider Business Needs: Align control selection with the organization's operational requirements and strategic objectives.
Step 3: Define Responsibilities
Clearly defining who is responsible for implementing and managing each control is crucial. Responsibilities should be assigned to individuals who have the authority and competence to manage the specific controls effectively.
- Assign Roles and Responsibilities: Designate information security roles, such as a Security Officer or IT Manager, who will oversee the implementation of the controls.
- Ensure Accountability: Make sure each role involved with the ISMS has clear responsibilities and is held accountable for their part in the security measures.
Step 4: Implement Controls
Implement the selected controls as per the guidance provided in ISO 27002. This may involve configuring technologies, developing policies and procedures, training staff, and any other actions necessary to activate the control.
- Develop Policies and Procedures: Create or update security policies and procedures that reflect the implemented controls.
- Deploy Technologies: Install and configure security technologies such as firewalls, encryption, and access control systems.
- Conduct Training: Educate employees about their roles in the ISMS, including how to adhere to new policies and how to respond to security incidents.
Step 5: Monitor and Review
After implementation, it's important to continuously monitor the effectiveness of the controls and make improvements where necessary. This involves regular audits, reviews, and updates to the ISMS.
- Continuous Monitoring: Use tools and techniques to regularly monitor security measures for effectiveness and compliance.
- Regular Audits: Conduct internal and external audits to ensure controls are functioning as intended and to identify areas for improvement.
- Review and Improve: Based on monitoring and audit results, make necessary adjustments to controls and processes to enhance the ISMS.
Step 6: Prepare for Certification
If seeking ISO 27001 certification, prepare for the certification audit by ensuring all documentation is complete and up to date, and that all employees are aware of their roles within the ISMS.
- Documentation Review: Ensure all ISMS documentation is comprehensive and up to date.
- Mock Audits: Conduct mock audits to prepare for the certification process and to identify any last-minute adjustments needed.
Implementing ISO 27001 controls is a dynamic and ongoing process that requires commitment across the organization. By following these steps, organizations can ensure that their ISMS not only meets ISO standards but also effectively protects their information assets against current and future threats. In the next section, we will explore the ISO 27001 certification process, detailing the steps organizations need to take to achieve and maintain certification.
ISO 27001 Certification Process
Achieving ISO 27001 certification is a significant milestone for any organization committed to information security. The certification not only demonstrates compliance with a globally recognized standard but also reassures clients and stakeholders of the organization's dedication to maintaining high security standards. Here is a step-by-step guide to the ISO 27001 certification process, designed to help organizations navigate this journey effectively.
Step 1: Establish the ISMS
Before an organization can undergo an ISO 27001 certification audit, it must establish a comprehensive Information Security Management System (ISMS) based on the standard’s requirements. This involves:
- Implementing ISO 27001 Controls: As previously discussed, select and implement the appropriate controls from Annex A based on the organization's risk assessment.
- Documentation: Develop all required documentation, including the scope of the ISMS, information security policy, Risk Treatment Plan (RTP), and Statement of Applicability (SoA).
Step 2: Perform an Internal Audit
An internal audit is crucial to determine whether the ISMS conforms to ISO 27001 standards as well as to the organization's own requirements.
- Check Compliance: The internal audit should cover all aspects of the standard, ensuring that policies and controls are not only implemented but are also effective in managing risks.
- Identify Gaps: This is an opportunity to identify any shortcomings or areas where the ISMS does not meet the standard, allowing for adjustments before the external audit.
Step 3: Management Review
The results of the internal audit, along with performance data from the ISMS, should be reviewed by top management. This ensures leadership engagement and support, which are essential for the certification process.
- Evaluate ISMS Performance: Management should evaluate whether the ISMS is achieving its intended outcomes and if it is effective in managing risks.
- Resource Allocation: Ensure that necessary resources are available to maintain and improve the ISMS.
Step 4: Corrective Actions
Based on the internal audit and management review, take corrective actions to address any identified issues. This step is vital to ensure the ISMS is fully compliant with ISO 27001 before undergoing the certification audit.
- Implement Changes: Make any necessary changes to the ISMS processes, controls, or documentation.
- Document Actions: Keep a record of what was changed, why, and what the outcomes were.
Step 5: Certification Audit
The certification audit is conducted by an external ISO 27001 auditor from an accredited certification body. This audit is performed in two stages:
- Stage 1: Preliminary audit to review ISMS documentation, policies, and scope. This stage checks readiness for the full audit.
- Stage 2: Comprehensive audit that assesses the effectiveness of the ISMS in detail, including compliance with all parts of ISO 27001.
Step 6: Continual Improvement
After achieving certification, the organization must enter a cycle of continual improvement to maintain compliance. This involves regular monitoring and reviewing of the system, implementing improvements, and periodic re-certification audits.
- Ongoing Monitoring and Reviews: Regularly monitor the ISMS against the set objectives and the evolving threat landscape.
- Surveillance Audits: Typically conducted annually by the certification body to ensure ongoing compliance.
By following these steps, organizations can successfully navigate the path to ISO 27001 certification, securing not only a significant competitive advantage but also a robust foundation for managing information security risks effectively. This strategic approach ensures that the ISMS remains dynamic and responsive to both current and future security challenges. In the concluding section, we will recap the importance of ISO 27001 controls and the benefits of achieving certification.
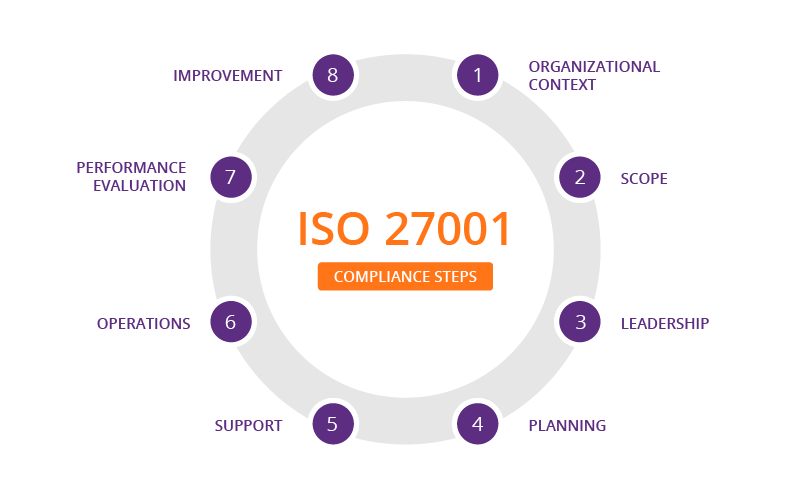
Developing an ISO 27001 Compliance Strategy
For organizations aiming to enhance their information security management, developing a comprehensive ISO 27001 compliance strategy is crucial. This strategy not only facilitates successful certification but also ensures that information security is woven into the fabric of organizational operations, enhancing resilience and trust. Here’s how organizations can develop and maintain an effective ISO 27001 compliance strategy.
Understanding Organizational Context and Defining Scope
The first step in developing a compliance strategy is understanding the organizational context and defining the scope of the ISMS. This includes identifying the business processes that need protection and the information assets that are critical to the organization’s operations.
- Determine Scope: Clearly define what departments, processes, and physical locations will be included in the ISMS.
- Business Needs and Objectives: Align the ISMS with the overall business objectives and requirements of the organization
Risk Assessment and Control Selection
An effective strategy requires a thorough risk assessment process as the foundation for control selection and implementation.
- Conduct Risk Assessments: Regularly assess risks to identify potential security threats and vulnerabilities.
- Select Appropriate Controls: Choose controls from ISO 27001 Annex A that are most relevant to the identified risks and tailor them to the organizational context.
Resource Allocation and Management Commitment
Securing commitment and resources from management is essential for implementing and maintaining the ISMS.
Management Support: Obtain executive support to ensure that information security is prioritized within the organization.
Allocate Resources: Ensure adequate resources are available for implementing and maintaining the ISMS, including budget, personnel, and technology.
Training and Awareness
A successful compliance strategy also depends on the awareness and competence of the personnel involved.
- Employee Training: Conduct regular training sessions to educate employees about their roles in the ISMS and the importance of information security.
- Awareness Programs: Develop ongoing awareness programs to keep security at the forefront of organizational culture.
Monitoring, Auditing, and Continuous Improvement
Continuous monitoring and regular audits are key to ensuring the effectiveness of the ISMS and fostering continual improvement.
- Continuous Monitoring: Implement processes to continuously monitor the effectiveness of the ISMS.
- Regular Audits: Conduct internal and external audits to assess compliance with ISO 27001 and the effectiveness of implemented controls.
- Review and Improve: Use audit results and monitoring data to drive continual improvement of the ISMS.
Prepare for Changes and Updates
Stay informed about updates to ISO 27001 standards and adjust the ISMS accordingly to ensure ongoing compliance.
Regulatory Updates: Keep abreast of changes in legal, regulatory, and technical standards affecting information security.
Adapt and Update: Regularly update the ISMS to reflect changes in the business environment, technology, and emerging threats.
By systematically developing and implementing an ISO 27001 compliance strategy, organizations can not only achieve certification but also integrate robust information security practices into their daily operations. This strategic approach helps in managing risks more effectively and ensures that information security evolves in line with organizational growth and changes.
Conclusion
ISO 27001 controls are central to establishing a secure and resilient information security management system. By understanding and implementing these controls effectively, organizations can protect their information assets against a wide array of threats. Achieving ISO 27001 certification demonstrates an organization's commitment to information security, enhancing its reputation and building trust with clients and stakeholders.
The journey to ISO 27001 compliance and certification requires a strategic approach, meticulous planning, and ongoing commitment. However, the benefits of securing critical information assets and enhancing business resilience make this investment worthwhile. As security threats evolve, adherence to ISO 27001 helps organizations stay prepared and responsive, turning information security into a strategic asset rather than a compliance obligation.

